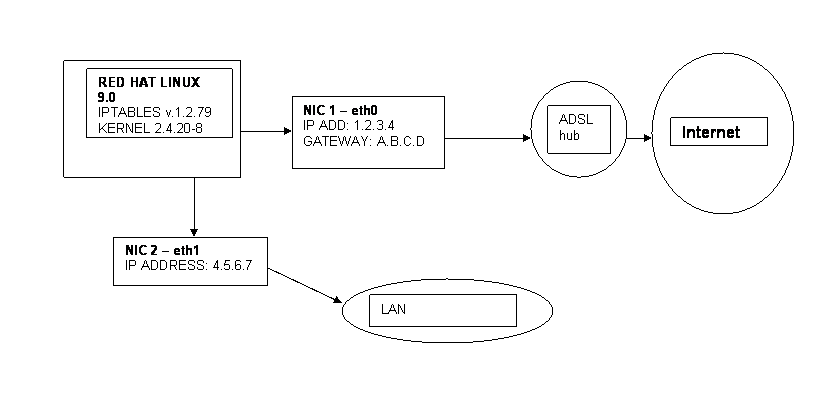
Dear all
I want to share internet access on
my LAN and my configurations are as below. (see picture)
Is my NAT configuration correct? I
want to allow only some users to access the internet-and check mail using
outlook express.
Thanks for
helping.
Rgds
gy
iptables –vnL
> Chain INPUT
(policy DROP 485 packets, 51391 bytes)
> pkts bytes target prot
opt in out
source
> destination
> 0 0
ACCEPT tcp --
* *
0.0.0.0/0
>
0.0.0.0/0 tcp
spt:53
> 21 4504
ACCEPT udp --
* *
0.0.0.0/0
>
0.0.0.0/0 udp
spt:53
> 0 0
ACCEPT udp --
* *
0.0.0.0/0
>
0.0.0.0/0 udp
spt:80
> 813 704K
ACCEPT tcp --
* *
0.0.0.0/0
>
0.0.0.0/0 tcp
spt:80
> 0 0
ACCEPT udp --
* *
0.0.0.0/0
>
0.0.0.0/0 udp
spt:443
> 16 3793
ACCEPT tcp --
* *
0.0.0.0/0
>
0.0.0.0/0 tcp
spt:443
> 0 0
ACCEPT tcp --
* *
0.0.0.0/0
>
0.0.0.0/0 state
RELATED,ESTABLISHED
> 0 0
ACCEPT all -- lo
*
0.0.0.0/0
> 0.0.0.0/0
>
> Chain FORWARD (policy
DROP 0 packets, 0 bytes)
> pkts bytes target prot
opt in out
source
> destination
> 0 0
ACCEPT all -- eth1
eth0
0.0.0.0/0
>
0.0.0.0/0 state
RELATED,ESTABLISHED
> 0 0
ACCEPT all -- eth0
eth1
0.0.0.0/0
> 0.0.0.0/0
>
> Chain OUTPUT (policy
ACCEPT 3465 packets, 286K bytes)
> pkts bytes target prot
opt in out
source
> destination
> [root@rh9 root]# iptables -t nat
-L
> Chain PREROUTING
(policy ACCEPT)
> target prot opt
source
destination
>
> Chain POSTROUTING
(policy DROP)
> target prot opt
source
destination
> MASQUERADE all --
anywhere
anywhere
>
> Chain OUTPUT (policy
ACCEPT)
> target prot opt
source
destination