On Thu, May 3, 2018 at 9:29 AM Dunson, Jarrell R <jrdu235@xxxxxxxxx> wrote:
Ok ... some of the guidance I see/hear refers to the setting up a .ssh/authorized_keys directory for each user that logs in ... However, if I understand correctly (?) this would be the case for individuals... logging onto some other remote server?
Correct. SSH keys are for logging into the server directly. (There are some situations when you would want to be able to log in as the use HTTPD is running as - for example, some continous deployment schemes, but that isn't usually necessary.)
For the set up of a https-enabled website, then, you are saying I don't need to set up an .ssh/authorized_keys file?
In other words, for Apache, I would only need to use something like this in my httpd-vhosts.conf file
NameVirtualHost *:443
<VirtualHost *:443>ServerName www.yoursite.comDocumentRoot /var/www/siteSSLEngine onSSLCertificateFile /path/to/www_yoursite_com.crtSSLCertificateKeyFile /path/to/www_yoursite_com.keySSLCertificateChainFile /path/to/DigiCertCA.crt</VirtualHost>
You didn't say which version of HTTPD you are using, but NameVirtualHost isn't used in 2.4.
That does look like a reasonable starter configuration.
You might want to make sure you have logging enabled - many people like to have separate logs for each vhost.
ErrorLog ${APACHE_LOG_DIR}/sitename_error.log
CustomLog ${APACHE_LOG_DIR}/sitename_access.log combined
If your SSLCertificateFile has the chain in it (LetsEncrypt certificates do by default), then you don't need SSLCertificateChainFile.
There are some other security settings you might want to change. You can check your site at https://www.ssllabs.com/ssltest/ to see how secure it is.
Also, it seem some administrators include / configure the httpd-ssl.conf file, and others do not... they just use the httpd-vhosts.conf file (?) ... do we need to use httpd-ssl.conf ?
You can put any configuration in any file you want. Debian/Ubuntu recommend having one file for each site you are serving.
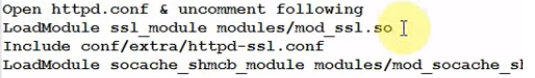
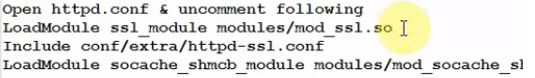
You do need mod_ssl to be loaded, but that is usually in the main config file - or for Debian/Ubuntu, in a separate config file for the specific module.
Any guidance would help...
thanks
Jarrell
On 5/2/2018 4:59 PM, Eric Covener wrote:
On Wed, May 2, 2018 at 4:53 PM, Dunson, Jarrell R <jrdu235@xxxxxxxxx> wrote:Hey all, for a new web server, so we need to create a .ssh directory and store the public key in .ssh/authorized_keys? If so, where does doe the directory need to be placed - underneath DocumentRoot?Your ssh setup shouldn't have anything to do with your webserver. --------------------------------------------------------------------- To unsubscribe, e-mail: users-unsubscribe@xxxxxxxxxxxxxxxx For additional commands, e-mail: users-help@xxxxxxxxxxxxxxxx
-- Jarrell R. Dunson, III Associate Director, Information Services University of Kentucky Office of Philanthropy Lexington, KY 40506-0015 859-257-5613 www.uky.edu/philanthropy