|
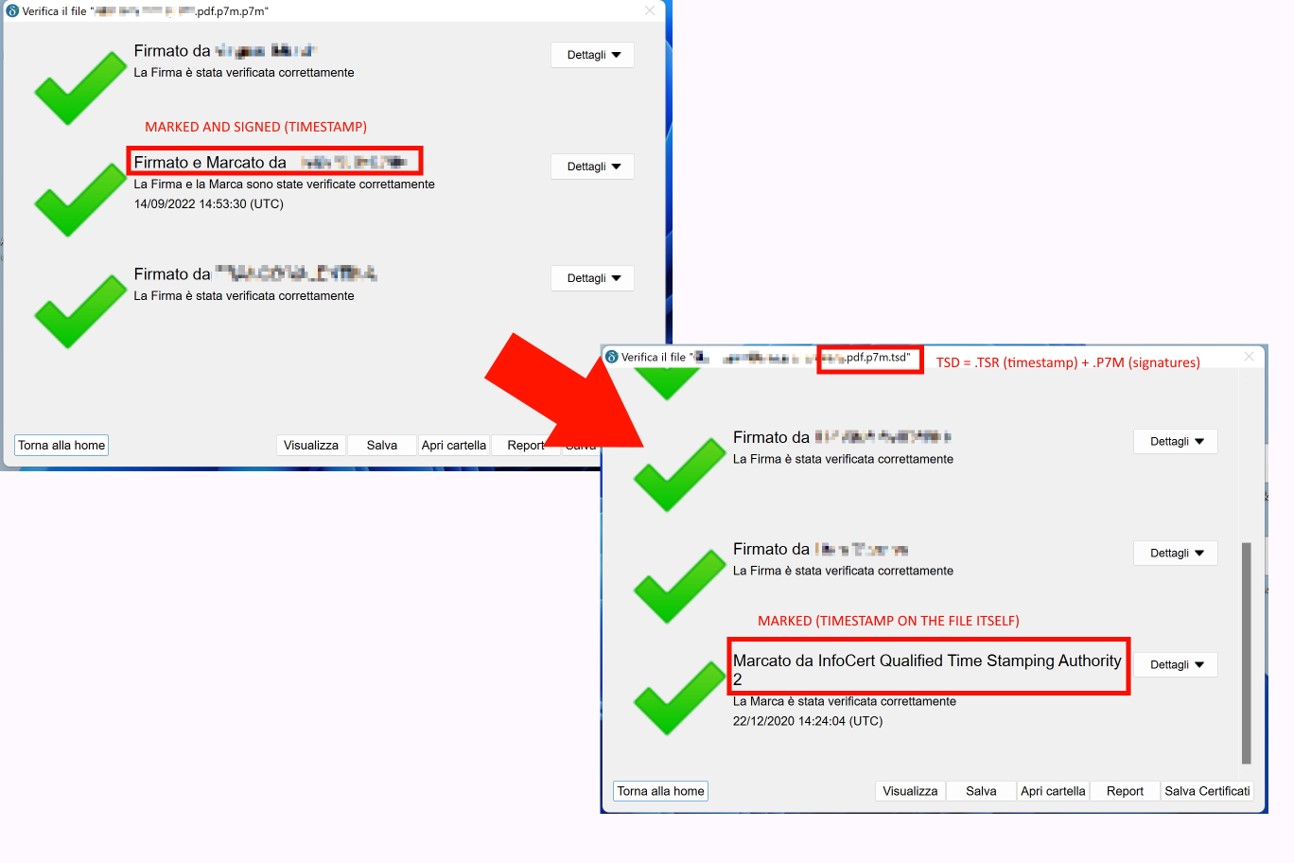
Hi, I signed a file with Infocert timestamp but due to an error I did the timestamp under the “signature level” and I’ve obtained this .p7m file with three signatures, which one of them appears with the timestamp attached on it. What I really
need, is the .tsd file with both the three signatures and the timestamp (kind of splitted from the signatures itself). Is there a way to “extract” this specific timestamp, like extracting its .TSR / .TST files, in order to attach it to the .p7m file itself, and obtain an .TSD file, how you can see in the attachments?
Since the timestamp was probably not executed on the file but on the signature itself, I guess I should first get the hashed .TSQ of the .p7m file, and next, I should generate a new .TSR / .TST (could I extract the .PEM certificates from
the previous timestamps in order to accomplish this step with the -TS reply -queryfile -inkey -signature)? My original idea, if it can work, was just "changing the level of the timestamp”: extracting the .TSR/.TST from the .P7M, and attaching “as it is” to
the file in order to get that .TSD or .M7M file: I’m just not sure if it’s that easy because I learned the .TSR is generated from the .TSQ of the file. As an alternative, I thinked of generating another .TSR file with a self-signed certificate in order to backdate its timestamp. I obtained the .TSR file but I don’t know how to merge it now to the .P7M file in order to get the .TSD (Dike
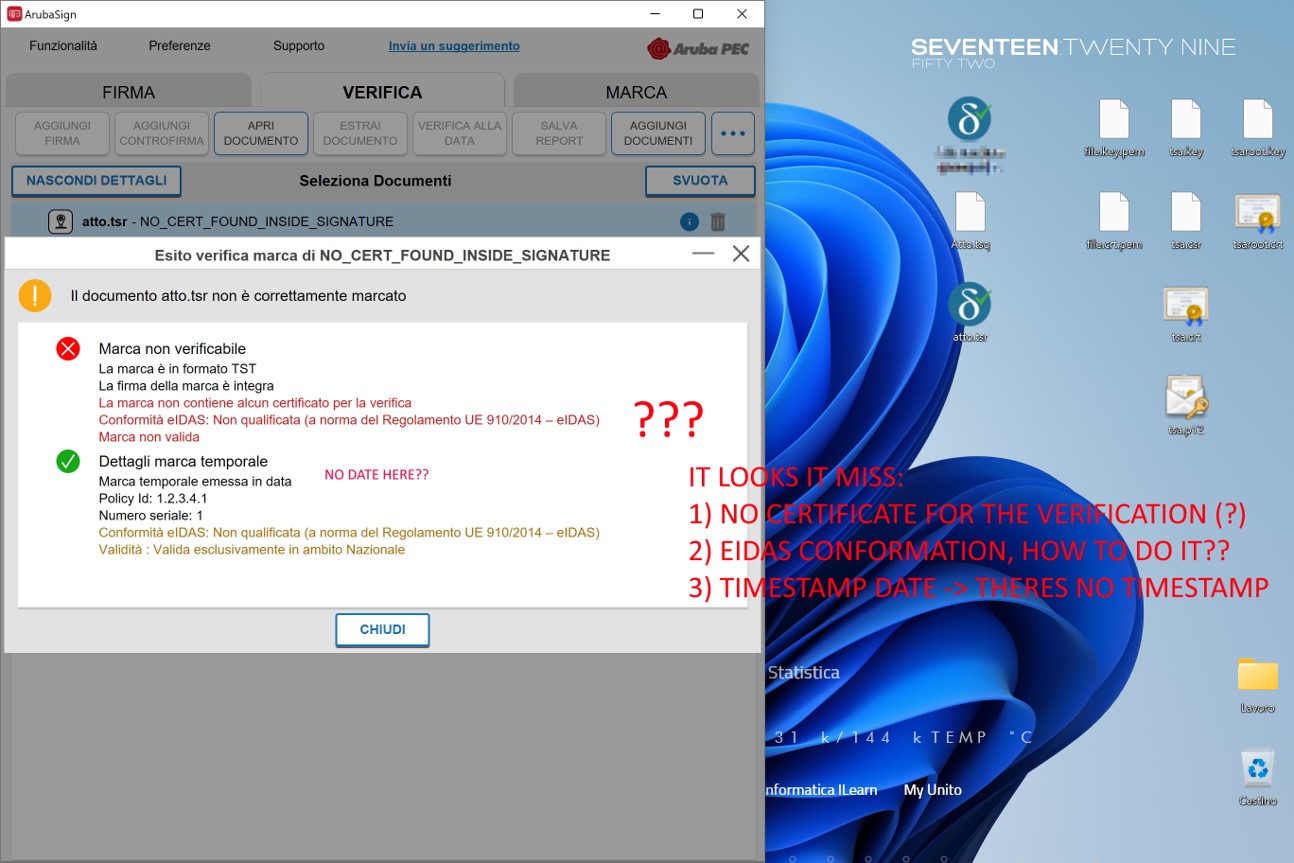
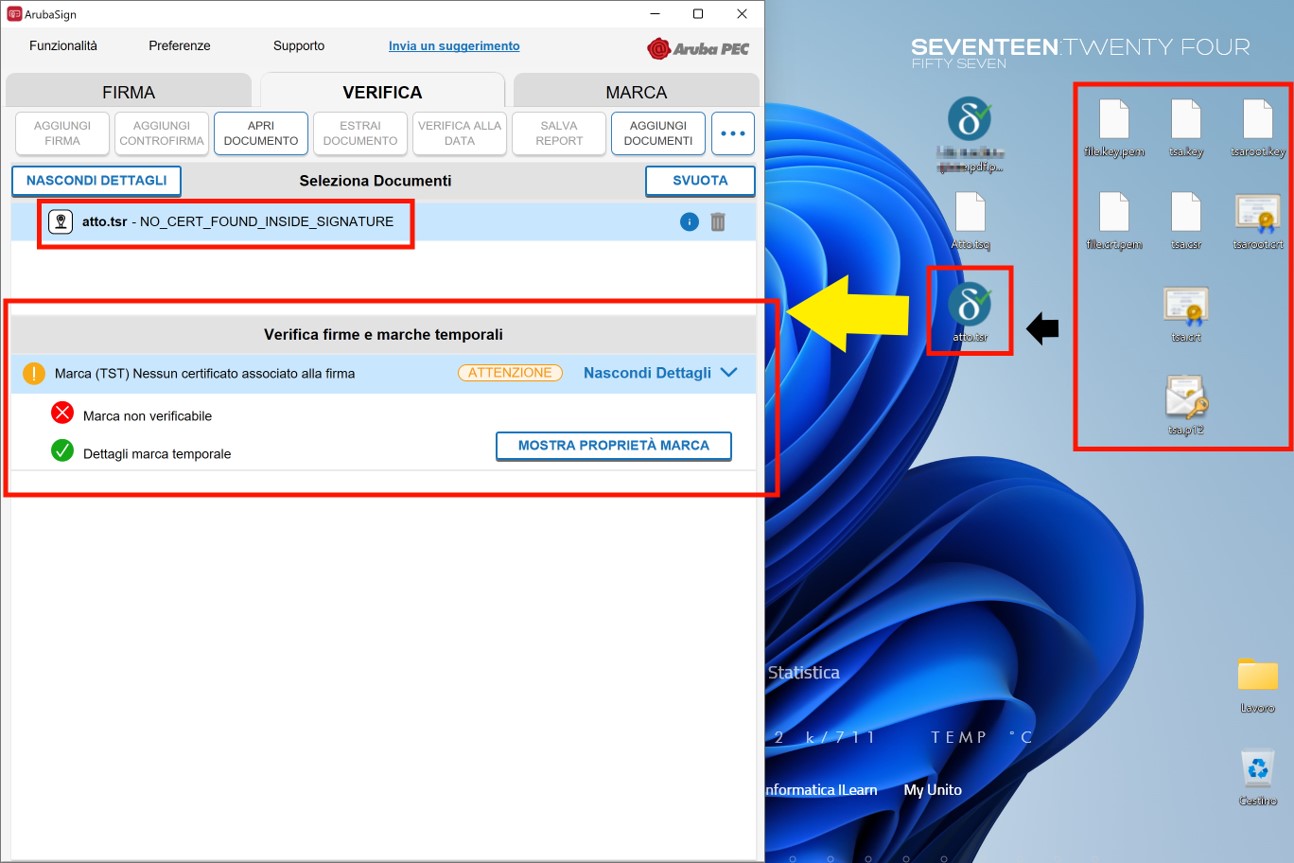
require a .TST file). Also, it looks this generated .TSR file does miss a valid certificate (not sure what it means), it doesn’t have any timestamp (I need to backdate it in order to match it to the other .P7M timestamp, I’m not sure at what steps I can put
the timestamp), and it is not conformed to the EIDAS specification (a self-signed certificate could be conformed? Or this specification just refers to accredited TSA autorities and there’s no way I can get it for this .TSR?).
The steps I made in order to generate this .TSR of the .P7M file, are these:
Note: I didn’t touch anything before executing those commands, I just installed OpenSSL binary for Windows. I also had to “comment” those lines in the openssl.cfg file because the compiler was not finding the demoCA folders at the latest
step: # certificate = $dir/cacert.pem # The CA certificate # certs = $dir/cacert.pem # Certificate chain to include in reply Thanks so much if you can help me |