Hi,
--
Stiju Easo
The unexamined life is not worth living for man.
Socrates, in Plato, Dialogues, Apology
Greek philosopher in Athens (469 BC - 399 BC)
I had a tool similar to SSLDump , which could decrypt SSL traffic (like Man in Middle).
for this, I used to copy needed data to SSL* and used to call tls1_enc/ssl3_enc to decrypt data.
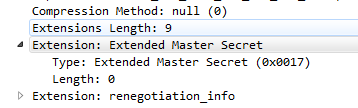
Everything used to work fine extended master secret came up in SSL header,
even if it has empty value (just the place holder) as in pic attached.

the SSL decryption failed, with -1 error from tls1_enc
"-1: if the record's padding/AEAD-authenticator is invalid or, if sending,
an internal error occurred."
on further debugging failure happens in EVP_Cipher().
I tried OpenSSL1.1 and OpenSSL1.0.2, both has the same behavior.
the doubt I have is
1) if I have Extended Master Secret Extention type (with value 0) in my data, should I need to set something to SSL context so that.
2) Is it necessary to use OpenSSL 1.1.0, if I don't intend to use value appearing in ExtendedMasterSecret? I just want to ignore wat ever appearing in the header as of now. for this will 1.0.2 will do, given I resolve item (1)
Stiju Easo
The unexamined life is not worth living for man.
Socrates, in Plato, Dialogues, Apology
Greek philosopher in Athens (469 BC - 399 BC)
-- openssl-users mailing list To unsubscribe: https://mta.openssl.org/mailman/listinfo/openssl-users
