After digging source code for more than a week I feel I need help :)
We’re creating SCTP server side, when client sends INIT to our primary IP things are fine.
But when client sends INIT to our secondary IP… Linux 4.18.0 is sending INIT_ACK from our primary IP, which clients MUST understand...
https://datatracker.ietf.org/doc/html/rfc4960#section-5.1.2
> D) An INIT or INIT ACK chunk MUST be treated as belonging to an
> already established association (or one in the process of being
> established) if the use of any of the valid address parameters
> contained within the chunk would identify an existing TCB.
…yet our SCTP client (didn’t read that part of RFC) does not understand this INIT_ACK and fails to establish association :(
Client is some outdated soft/hardware that nobody knows how to configure properly, if that is at all possible.
So far I’ve found 20+ years old question without good answer
https://sourceforge.net/p/lksctp/mailman/lksctp-developers/thread/3E5A330C.E292CFDF%40us.ibm.com/#msg5265341
Maybe situation has changed and it became possible to influence the Kernel decision… so the source IP address of INIT_ACK IP packet be equal to destination IP address of INIT IP packet?
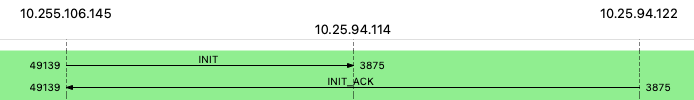
Attached a diagram and dump.
In this example we’d like frame 2 to have source address of 10.25.94.114
Alexander Petrossian
P.S. Wireshark dump:
No. Time Source Destination Protocol Length Info otid dtid Type Session
1 0.000000 10.255.106.145 10.25.94.114 SCTP 156 INIT
Frame 1: 156 bytes on wire (1248 bits), 156 bytes captured (1248 bits)
Linux cooked capture v1
Internet Protocol Version 4, Src: 10.255.106.145 (10.255.106.145), Dst: 10.25.94.114 (10.25.94.114)
Stream Control Transmission Protocol, Src Port: 49139 (49139), Dst Port: 3875 (3875)
Source port: 49139
Destination port: 3875
Verification tag: 0x00000000
[Association index: disabled (enable in preferences)]
Checksum: 0x98d014aa [unverified]
[Checksum Status: Unverified]
INIT chunk (Outbound streams: 8, inbound streams: 8)
Chunk type: INIT (1)
Chunk flags: 0x00
Chunk length: 108
Initiate tag: 0x7ff58ed1
Advertised receiver window credit (a_rwnd): 1000000
Number of outbound streams: 8
Number of inbound streams: 8
Initial TSN: 457141724
IPv4 address parameter (Address: 10.255.106.209)
IPv4 address parameter (Address: 10.255.106.145)
Supported address types parameter (Supported types: IPv4)
ECN parameter
Supported Extensions parameter (Supported types: AUTH)
Forward TSN supported parameter
Random parameter
Requested HMAC Algorithm parameter (Supported HMACs: SHA-1)
Authenticated Chunk list parameter (Chunk types to be authenticated: )
No. Time Source Destination Protocol Length Info otid dtid Type Session
2 0.000059 10.25.94.122 10.255.106.145 SCTP 420 INIT_ACK
Frame 2: 420 bytes on wire (3360 bits), 420 bytes captured (3360 bits)
Linux cooked capture v1
Internet Protocol Version 4, Src: 10.25.94.122 (10.25.94.122), Dst: 10.255.106.145 (10.255.106.145)
Stream Control Transmission Protocol, Src Port: 3875 (3875), Dst Port: 49139 (49139)
Source port: 3875
Destination port: 49139
Verification tag: 0x7ff58ed1
[Association index: disabled (enable in preferences)]
Checksum: 0x9df2bf8e [unverified]
[Checksum Status: Unverified]
INIT_ACK chunk (Outbound streams: 8, inbound streams: 8)
Chunk type: INIT_ACK (2)
Chunk flags: 0x00
Chunk length: 372
Initiate tag: 0xded810ed
Advertised receiver window credit (a_rwnd): 212992
Number of outbound streams: 8
Number of inbound streams: 8
Initial TSN: 676475653
IPv4 address parameter (Address: 10.25.94.122)
IPv4 address parameter (Address: 10.25.94.114)
State cookie parameter (Cookie length: 324 bytes)
ECN parameter
Forward TSN supported parameter

