I should mention that a hacker found this vulnerability and sent me the URL.
I'm reasonably confident this isn't coming from my PHP application.
The text from the path_info is turning up in the <body>, here's a screenshot
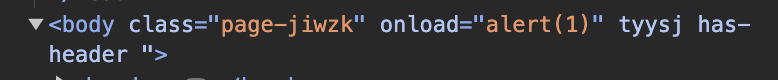
But my PHP code generates this <body> code like this:
<body class="page-<?= $filename ?> <?= $hasHeader ? 'has-header' : '' ?> <?= $hasSideMenu ? 'has-side-menu' : '' ?>">
Hmmm, that looks suspiciously like the $filename causing the problem....where does that come from?
$filename = pathinfo($_SERVER['PHP_SELF'], PATHINFO_FILENAME);
PHP_SELF is including the script and also the path_info - darn!
Changed to SCRIPT_NAME which is just the script name.
$filename = pathinfo($_SERVER['SCRIPT_NAME'], PATHINFO_FILENAME);
Sorry - this is clearly my problem... but thank you Frank for the pointer in the right direction.
Cheers
Murray
