Use mod_info to look at the actual loaded configuration and see what SSLCipherSuite values are being loaded and where they are coming from.
- Y
Sent from a device with a very small keyboard and hyperactive autocorrect.
On Mon, Oct 24, 2022, 5:20 AM Kaushal Shriyan <kaushalshriyan@xxxxxxxxx> wrote:
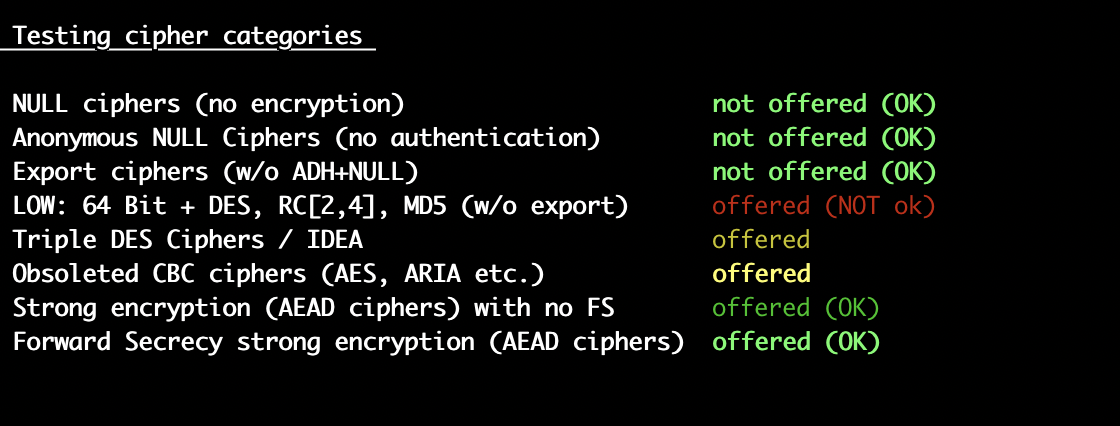
On Fri, Oct 21, 2022 at 8:51 AM Kaushal Shriyan <kaushalshriyan@xxxxxxxxx> wrote:On Thu, Oct 20, 2022 at 11:14 PM Kaushal Shriyan <kaushalshriyan@xxxxxxxxx> wrote:Hi,I am running Server version: Apache/2.4.54 (IUS) on CentOS Linux release 7.9.2009 (Core). I have enabled the SSLCipherSuite based on https://ssl-config.mozilla.org/#server=apache&version=2.4.54&config=intermediate&openssl=1.1.1k&guideline=5.6 in httpd config /etc/httpd/conf.d/ssl.confSSLCipherSuite ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384LOW: 64 Bit + DES, RC[2,4], MD5 (w/o export) offered (NOT ok)
Triple DES Ciphers / IDEA offered
Obsoleted CBC ciphers (AES, ARIA etc.) offered[kaushal@ ~]$ httpd -v
Server version: Apache/2.4.54 (IUS)
Server built: Jul 20 2022 23:47:24
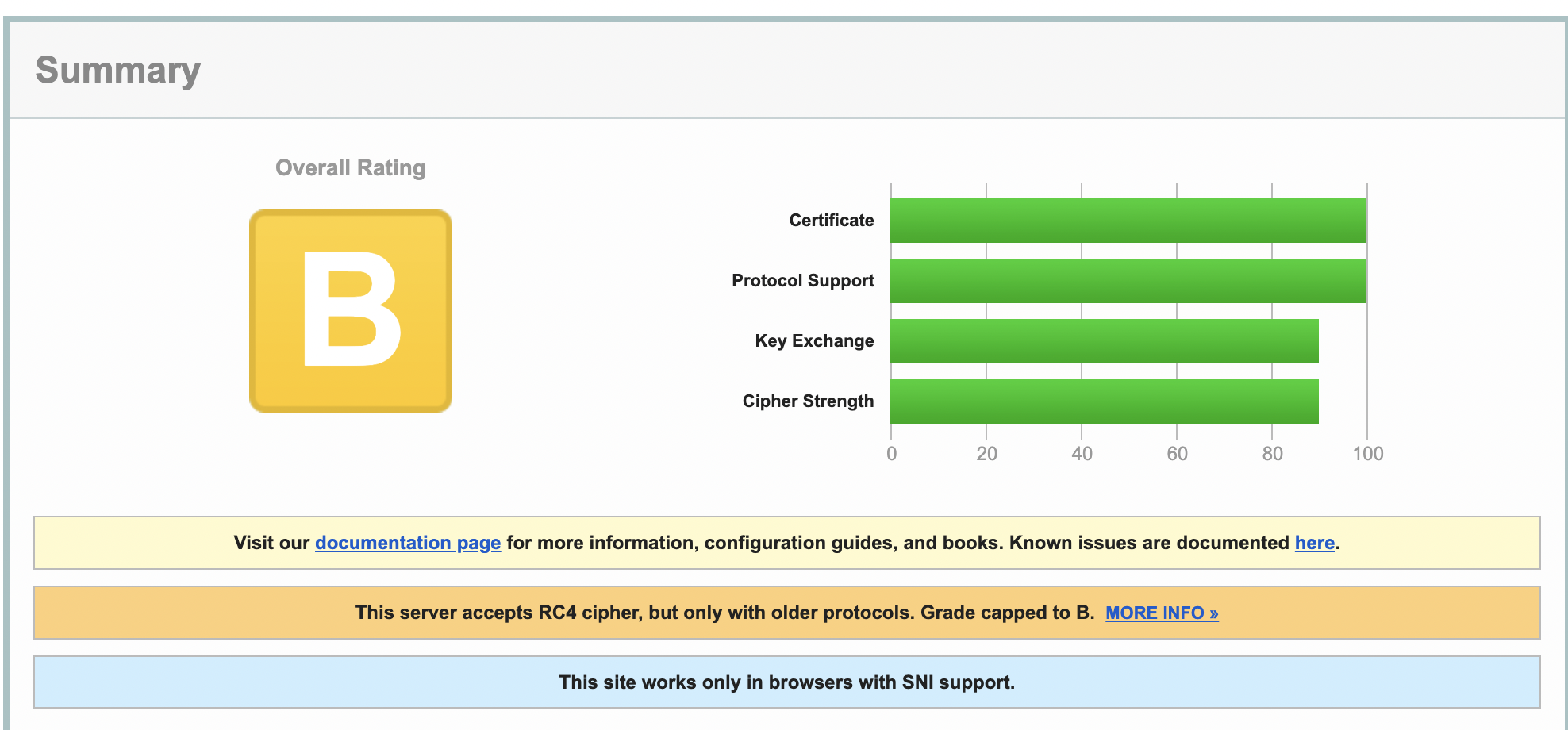
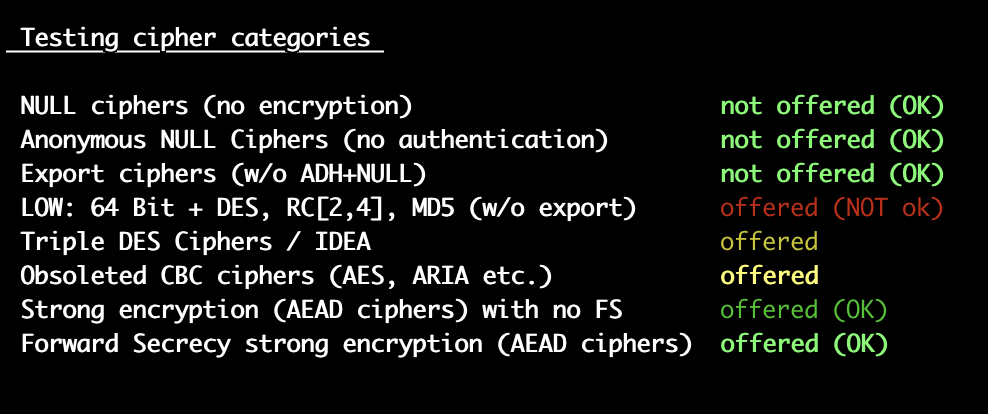
[kaushal@ ~]$Is there a way to have the Overall rating as A? This server accepts RC4 cipher, but only with older protocols. Grade capped to B as per https://blog.qualys.com/product-tech/2013/03/19/rc4-in-tls-is-broken-now-what?_ga=2.190316584.2048888948.1666268705-2031408266.1660632196Please guide me. Thanks in advance.Best Regards,KaushalHi,Further to my earlier email, I have enabled the SSLCipherSuite based on https://ssl-config.mozilla.org/#server=apache&version=2.4.54&config=intermediate&openssl=1.1.1k&guideline=5.6 in httpd config /etc/httpd/conf.d/ssl.conf.SSLCipherSuite ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384LOW: 64 Bit + DES, RC[2,4], MD5 (w/o export) offered (NOT ok)
Triple DES Ciphers / IDEA offered
Obsoleted CBC ciphers (AES, ARIA etc.) offered[kaushal@ ~]$ httpd -v
Server version: Apache/2.4.54 (IUS)
Server built: Jul 20 2022 23:47:24
[kaushal@ ~]$Is there a way to have the Overall rating as A? This server accepts RC4 cipher, but only with older protocols. Grade capped to B as per https://blog.qualys.com/product-tech/2013/03/19/rc4-in-tls-is-broken-now-what?_ga=2.190316584.2048888948.1666268705-2031408266.1660632196 I have followed https://access.redhat.com/solutions/6688001 but the issue still persists.$nmap -sV --script ssl-enum-ciphers -p 443 example.domain.comPORT STATE SERVICE VERSION
443/tcp open ssl/http Apache httpd 2.4.54 ((IUS) OpenSSL/1.0.2k-fips)
|_http-server-header: Apache/2.4.54 (IUS) OpenSSL/1.0.2k-fips
| ssl-enum-ciphers:
| TLSv1.2:
| ciphers:
| TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 (secp256r1) - A
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 (secp256r1) - A
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (secp256r1) - A
| TLS_DHE_RSA_WITH_AES_256_GCM_SHA384 (dh 2048) - A
| TLS_DHE_RSA_WITH_AES_256_CBC_SHA256 (dh 2048) - A
| TLS_DHE_RSA_WITH_AES_256_CBC_SHA (dh 2048) - A
| TLS_DHE_RSA_WITH_CAMELLIA_256_CBC_SHA (dh 2048) - A
| TLS_RSA_WITH_AES_256_GCM_SHA384 (rsa 2048) - A
| TLS_RSA_WITH_AES_256_CBC_SHA256 (rsa 2048) - A
| TLS_RSA_WITH_AES_256_CBC_SHA (rsa 2048) - A
| TLS_RSA_WITH_CAMELLIA_256_CBC_SHA (rsa 2048) - A
| TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 (secp256r1) - A
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256 (secp256r1) - A
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (secp256r1) - A
| TLS_DHE_RSA_WITH_AES_128_GCM_SHA256 (dh 2048) - A
| TLS_DHE_RSA_WITH_AES_128_CBC_SHA256 (dh 2048) - A
| TLS_DHE_RSA_WITH_AES_128_CBC_SHA (dh 2048) - A
| TLS_DHE_RSA_WITH_SEED_CBC_SHA (dh 2048) - A
| TLS_DHE_RSA_WITH_CAMELLIA_128_CBC_SHA (dh 2048) - A
| TLS_RSA_WITH_AES_128_GCM_SHA256 (rsa 2048) - A
| TLS_RSA_WITH_AES_128_CBC_SHA256 (rsa 2048) - A
| TLS_RSA_WITH_AES_128_CBC_SHA (rsa 2048) - A
| TLS_RSA_WITH_SEED_CBC_SHA (rsa 2048) - A
| TLS_RSA_WITH_CAMELLIA_128_CBC_SHA (rsa 2048) - A
| TLS_ECDHE_RSA_WITH_3DES_EDE_CBC_SHA (secp256r1) - C
| TLS_DHE_RSA_WITH_3DES_EDE_CBC_SHA (dh 2048) - C
| TLS_RSA_WITH_3DES_EDE_CBC_SHA (rsa 2048) - C
| TLS_RSA_WITH_IDEA_CBC_SHA (rsa 2048) - A
| TLS_ECDHE_RSA_WITH_RC4_128_SHA (secp256r1) - C
| TLS_RSA_WITH_RC4_128_SHA (rsa 2048) - C
| TLS_RSA_WITH_RC4_128_MD5 (rsa 2048) - C
| compressors:
| NULL
| cipher preference: server
| warnings:
| 64-bit block cipher 3DES vulnerable to SWEET32 attack
| 64-bit block cipher IDEA vulnerable to SWEET32 attack
| Broken cipher RC4 is deprecated by RFC 7465
| Ciphersuite uses MD5 for message integrity
|_ least strength: C
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 47.71 secondsI too followed https://httpd.apache.org/docs/trunk/ssl/ssl_howto.html but the below issue still persistsPlease guide me. Thanks in advance.Best Regards,KaushalHi,I will appreciate it if someone can pitch in for my earlier post to this mailing list and need guidance in this regard. I look forward to hearing from you. Thanks in advance.Best Regards,Kaushal